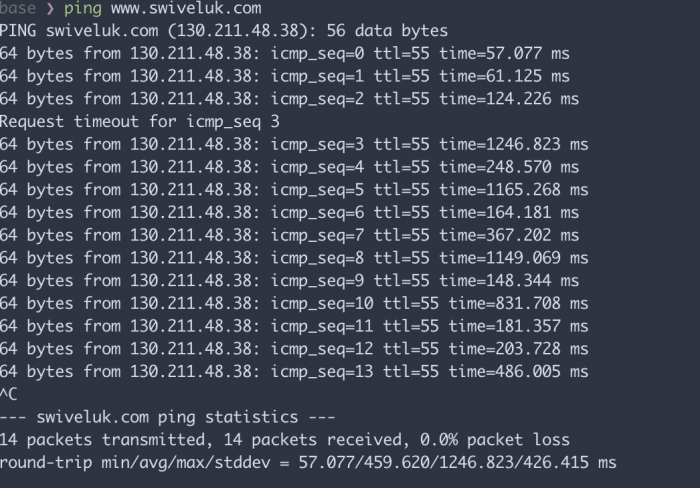
In the realm of network troubleshooting, a user issues a ping fe80 emerges as a valuable tool for diagnosing and resolving network issues. This comprehensive guide delves into the intricacies of ping fe80, providing a clear understanding of its role in IPv6 addressing and offering step-by-step troubleshooting techniques for common issues.
As we navigate the intricacies of network diagnostics, we will explore the security implications of issuing a ping fe80 and uncover advanced techniques for maximizing its effectiveness. By delving into related technologies and comparing ping fe80 with other network diagnostic tools, we aim to empower you with a comprehensive understanding of this essential troubleshooting tool.
Network Configuration
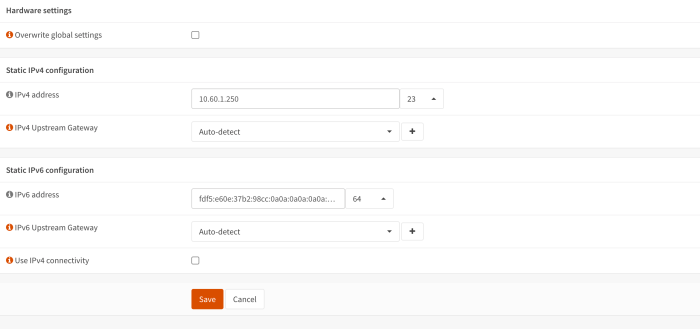
IPv6 addressing includes a unique fe80 link-local address for each network interface. This address is used for communication within the local network segment.
Issuing a ping fe80 is a diagnostic tool used to test the connectivity and reachability of devices on the same local network segment.
Role of fe80 in IPv6 Addressing
The fe80 address is automatically assigned to network interfaces when IPv6 is enabled. It has the following characteristics:
- It starts with fe80::/10 prefix.
- It is only valid within the local network segment.
- It is used for neighbor discovery and auto-configuration.
Issuing a ping fe80
To issue a ping fe80, open a command prompt or terminal window and enter the following command:
ping fe80::[interface address]
Replace [interface address]with the fe80 address of the network interface you want to test.
If the ping is successful, you will see replies from the device with the specified fe80 address.
Troubleshooting
Troubleshooting ping fe80 issues involves identifying the underlying causes and taking appropriate steps to resolve them. Common issues include network connectivity problems, incorrect IP address configuration, firewall settings, and hardware malfunctions. This section provides a step-by-step guide to diagnose and address these issues.
Before troubleshooting, ensure that the network configuration is correct and that the target device is reachable on the network.
Common Issues and Troubleshooting Steps
- Network Connectivity Issues:Check the physical network connections, such as cables and connectors, for any loose or damaged components. Verify that the network adapter is enabled and properly configured.
- Incorrect IP Address Configuration:Ensure that the IPv6 address and subnet mask on the source and destination devices are configured correctly. Use the
ifconfigoripconfigcommand to check the IP address configuration. - Firewall Settings:Check the firewall settings on both the source and destination devices to ensure that ICMP packets are allowed. ICMP is the protocol used by the ping command.
- Hardware Malfunctions:If all other troubleshooting steps fail, consider hardware malfunctions. Check the network adapter and other network hardware for any physical damage or defects.
Security Implications
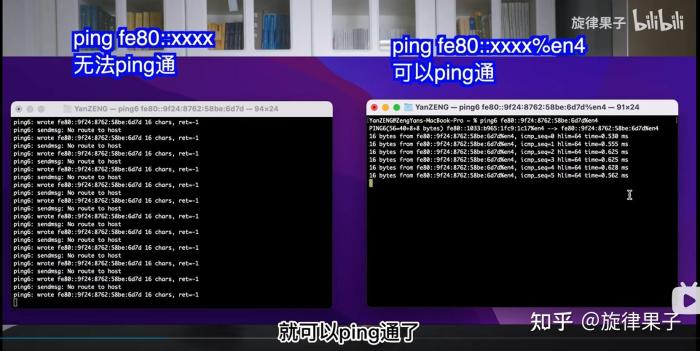
Issuing a ping fe80 can have several security implications:
Unauthenticated Access:Ping fe80 requests do not require authentication, making it easy for attackers to scan a network for active devices. This information can be used to identify potential targets for further attacks.
Denial-of-Service (DoS) Attacks:An attacker can send a large number of ping fe80 requests to a target device, overwhelming it with traffic and causing it to become unresponsive.
Mitigation
To mitigate these risks, it is important to implement the following security measures:
- Use Strong Firewall Rules:Configure firewalls to block ping fe80 requests from untrusted sources.
- Enable IPsec or SSH:Use secure protocols like IPsec or SSH for remote management instead of ping fe80.
- Limit Access to Ping Utility:Restrict access to the ping utility to authorized users only.
Advanced Usage: A User Issues A Ping Fe80
In addition to its basic functionality, ping fe80 can be used for advanced network diagnostics. By utilizing advanced techniques, network administrators can gain deeper insights into network behavior and identify issues more effectively.
One advanced technique involves using ping fe80 with different packet sizes. By varying the packet size, it is possible to identify potential issues related to packet fragmentation or Maximum Transmission Unit (MTU) mismatches. For example, if a ping fe80 with a large packet size fails while a ping fe80 with a smaller packet size succeeds, it may indicate an MTU issue.
Packet Intervals
Another advanced technique is adjusting the packet interval. By modifying the time between each ping fe80 request, it is possible to assess network latency and identify potential bottlenecks. A consistent latency with short intervals may indicate a stable network, while fluctuating latency or high latency with longer intervals may suggest network congestion or other issues.
When a user issues a ping fe80, it sends a packet to a specific destination. This packet contains data about the sender and the destination, as well as a sequence number. The destination then responds with a packet that contains the same sequence number.
This process is used to test the connectivity between two devices. If the ping is successful, it means that the devices are connected and can communicate with each other. Abeka algebra 1 quiz 28 can be used to test the connectivity between two devices.
It is a free online tool that can be used to test the connectivity between two computers or between a computer and a router.
Multiple Targets
Ping fe80 can also be used to ping multiple targets simultaneously. This technique can be useful for identifying network issues affecting specific hosts or devices. By pinging multiple targets, it is possible to determine if the issue is isolated to a single device or if it affects the entire network.
Related Technologies
Ping fe80 is a valuable network diagnostic tool, but it is not the only one available. Other tools, such as traceroute, nslookup, and netstat, can provide complementary information that can help you troubleshoot network issues.
Traceroute, for example, can show you the path that packets take from your computer to a destination. This can be helpful for identifying network congestion or other problems that may be affecting your connection. Nslookup can be used to look up DNS records, which can be helpful for troubleshooting DNS issues.
Netstat can show you a list of all active network connections, which can be helpful for identifying unauthorized connections or other security issues.
Using Ping fe80 with Other Technologies, A user issues a ping fe80
Ping fe80 can be used in conjunction with other network diagnostic tools to provide a comprehensive network analysis. For example, you can use ping fe80 to test the connectivity to a remote host, and then use traceroute to see the path that packets take to reach that host.
This can help you identify network congestion or other problems that may be affecting your connection.
You can also use ping fe80 to test the DNS resolution of a hostname, and then use nslookup to look up the DNS records for that hostname. This can help you troubleshoot DNS issues.
Answers to Common Questions
What is the purpose of issuing a ping fe80?
Issuing a ping fe80 allows you to test IPv6 connectivity and identify network issues by sending an ICMPv6 echo request to a specified IPv6 address.
What are some common issues that can occur when issuing a ping fe80?
Common issues include incorrect IPv6 addressing, firewall blocking, and network configuration errors. This guide provides step-by-step troubleshooting techniques to resolve these issues.
How can I mitigate the security risks associated with issuing a ping fe80?
To mitigate security risks, use ping fe80 only on trusted networks and limit its use to authorized personnel. Additionally, consider implementing network security measures such as firewalls and intrusion detection systems.